Data Center in London with optimal location and built-to-suit options.
Green Mountain’s data center in London is strategically located on major fiber routes and close to key internet exchanges. We offer space in our existing data center as well as a prepared site for built-to-suit projects.
Space in existing building
Space in planned building
Power Capacity
Latency to The City
Situated in Romford, less than 10 miles from the major financial centers of the City and Docklands you find Green Mountains data center in London. It consists of an already existing data center with available capacity in addition to a prepared site for built-to-suit projects. The site can support up to 40MW of IT load and already has several strong UK enterprise customers as core tenants. The data center was previously known as Infinity SDC, but is now part of the Green Mountain portfolio of data centers
The existing data center building can offer a flexible mix of pre-built 2MW data halls and space to construct additional capacity, which can be delivered on a totally tailored basis. If you need more space to grow, the adjacent ready-to-build site can support 16MW of IT load. A two storey design with eight data halls is ready for construction but can be configured to meet specific client requirements.
Features
- Build Year: 2009 Total space in building: 11.000m2 Current fill rate: 52% Designed and built to TierIII specifications Land footprint: 8.6 acres Dedicated substation on site Flexible design which can be scaled up or down based on our clients’ requirements
- Space in planned building: 5760 m2 Land footprint: 4 acres Designed to TierIII specifications Time to market: 24 months Planned design: 8 x 2MW datahalls Dedicated substation on site Fully configurable according to client's needs
- Maximum cooling capacity: 40 MW Grid supplies: 2N Type of cooling solution: Chilled Water with free cooling Automatic Standby generators Power source: 100% certified renewable power
- 24/7 onsite security personnel Biometric access systems Man traps Intelligent video surveillance Type of fire supression system: Gas
- No. of independent fiber providers available: 10 No. of fully redundant meet-me-rooms: 2 Diverse fiber routes into building Office space for rent: 325 m2 (existing data center), 140 m2 (in planned building) Smart Hands Services
Flexible options and headroom to grow

From retail to wholesale colocation up to multi-MW custom built projects, we provide a full range of options. We know our clients are different and have different needs. Our data center in London can accomodate most requirements. You can start small and expand further on the same campus as your requirements demand more space and power.
Our facility is designed according to the TierIII specification and certified to the following ISO standards:
ISO9001 (Quality Management)
ISO20000 (IT Service Management)
ISO27001 (Information Security)
ISO45001 (Health and Safety)
ISO14001 (Environmental Management)
The campus is secured 24/7 and supported with a range of on-site support services.
In the center of everything
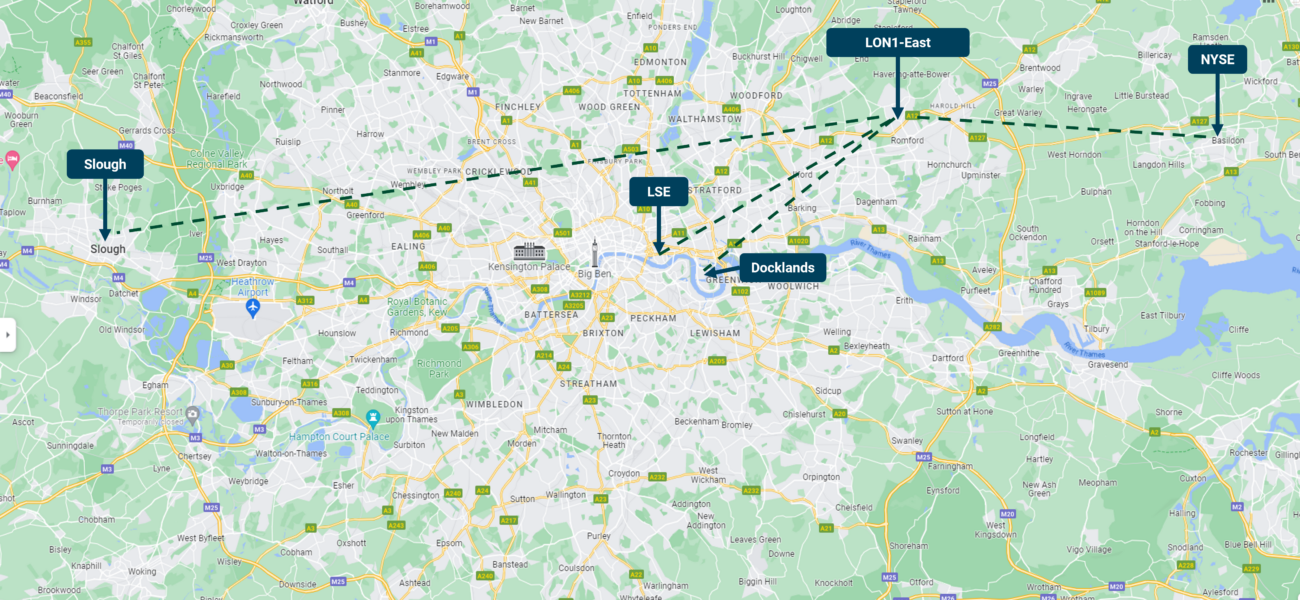
London is an extremely important data center hub and a must-have location for many international companies. However, available space and power in the region are limited, so the LON1-East is a rare opportunity to keep your data load in “the center of everything”. Our facility is equidistant between the LSE data center in the Docklands and the NYSE data center in Basildon, especially convenient for clients within the finance sector. The data center is located on major fiber routes and we have 10+ independent fiber providers available. This means rapid global connectivity and low latency. The LON1-East location provides a great opportunity to build multiple availability zones. Here are the latency numbers in the region:
Romford to Slough: 0.95 ms
Romford to The City: 1 ms
Romford to Docklands: 0,36 ms
If you don’t need all of your workload located in London, Green Mountain can offer balanced delivery models where you keep what you need close and the rest in a more cost-efficient and sustainable location. With our portfolio of data centers in Norway, we can offer clients the best of two worlds.
Future plans

Green Mountain’s vision is “Setting the green stanadard” in the data center industry, and our new London data center is no exception. The plan is to upgrade and modernize the current data center to meet Green Mountain’s strict sustainability standards.
The LON1– East data center will also be expanding further in 2024 with an additional 5,546 m2 of technical space to complement the existing 5,457m2 of white wall data hall space currently in operation. This space will provide an additional 8 data halls ranging in size from 896 sqm to 1,026 sqm, with 13.7MW of available IT load at an annualised design PUE of 1.2.
In addition to the expansion of the technical space, the existing office space will also be extended providing a further two floors of available office space, both measuring 650sqm, which can be further sub-divided to provide modular office space to meet our customers specific requirements.


